A cyberattack is a malicious and deliberate attempt to compromise the confidentiality, integrity, or availability of computer systems, networks, or data. These attacks are carried out by individuals, groups, or organizations with malicious intent and can take various forms, each with its own specific goals and methods. Cyberattacks can target a wide range of digital assets, including:
-
Phishing Attacks:
- Phishing attacks accounted for a significant portion of cyber incidents.
- In 2020, the Anti-Phishing Working Group (APWG) reported over 200,000 unique phishing websites each month.
- The number of phishing attacks continued to grow, targeting individuals and organizations.
-
Ransomware Attacks:
- Ransomware attacks were on the rise, with a noticeable increase in frequency and severity.
- In 2020, the average ransom demand increased significantly, with some demands reaching millions of dollars.
- Ransomware groups increasingly targeted critical infrastructure, healthcare, and government organizations.
-
Data Breaches:
- Data breaches exposed billions of records in recent years.
- Insider threats and misconfigured databases were common causes of data breaches.
- Industries such as healthcare, finance, and technology were frequently targeted.
-
DDoS Attacks (Distributed Denial of Service):
- DDoS attacks remained a prevalent threat.
- The number of DDoS attacks continued to grow, and attackers increasingly used amplification techniques to increase their impact.
- The targets ranged from websites to online services and critical infrastructure.
-
Malware:
- Malware threats evolved, with an emphasis on stealth and sophistication.
- Fileless malware attacks increased, making detection and mitigation more challenging.
- Banking trojans, ransomware, and spyware were common types of malware.
-
Zero-Day Vulnerabilities:
- Zero-day vulnerabilities were actively exploited by threat actors.
- Vulnerabilities in popular software and operating systems were a significant concern.
- Vulnerability disclosures and patches were crucial for mitigating these threats.
-
Social Engineering:
- Social engineering attacks, including pretexting and baiting, continued to be effective.
- Attackers used psychological manipulation to trick individuals into disclosing sensitive information or taking certain actions.
-
Supply Chain Attacks:
- Supply chain attacks gained prominence, with attackers targeting software and hardware supply chains.
- High-profile incidents raised awareness of the need for supply chain security.
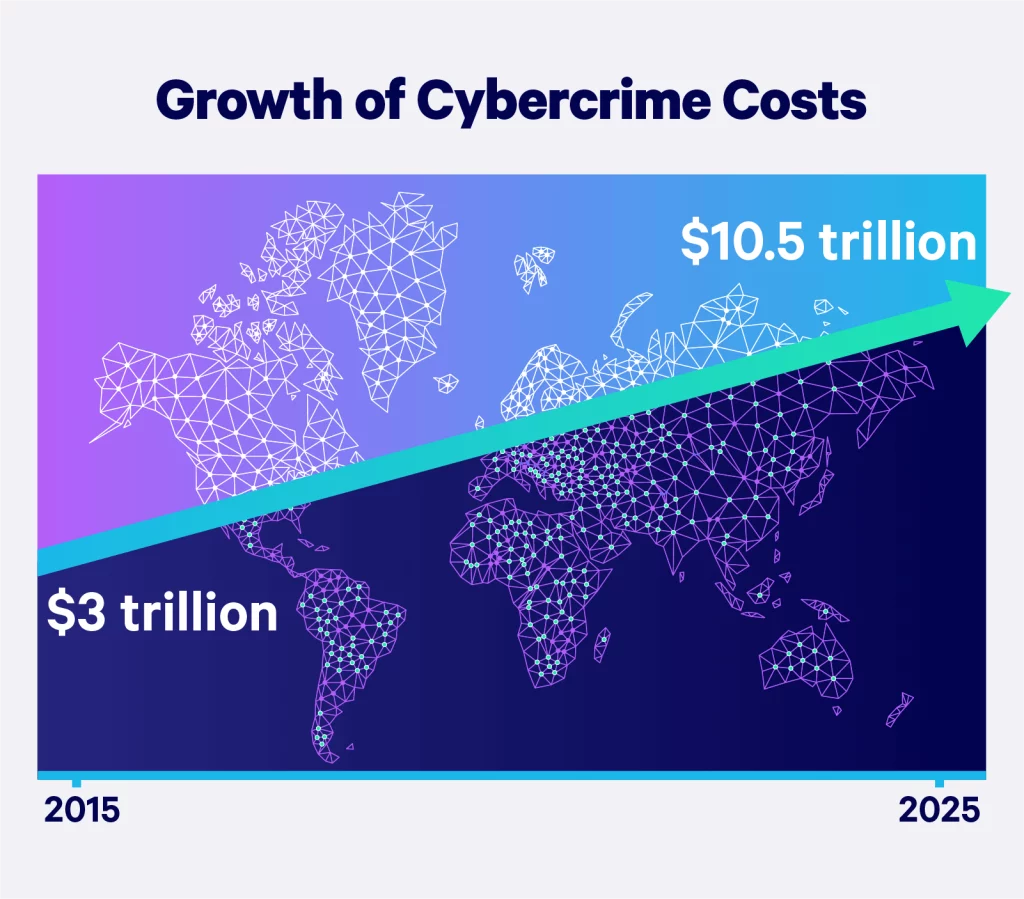
Cyberattacks pose a growing threat to businesses, especially small to medium-sized enterprises, with increasing frequency, sophistication, and precision. According to Accenture's Cost of Cybercrime Study, a staggering 43% of cyberattacks are directed at small businesses, but only 14% are adequately prepared to defend themselves.
A cyberattack not only disrupts normal business operations but can also inflict irreversible damage on critical IT assets and infrastructure, often beyond recovery due to budget and resource constraints.
Small businesses find themselves particularly vulnerable in this landscape. According to the Ponemon Institute's State of Cybersecurity Report, small to medium-sized businesses worldwide are grappling with:
- Insufficient Security Measures: 45% admit that their existing processes are inadequate at mitigating cyberattacks.
- Frequency of Attacks: A significant 66% have experienced a cyberattack within the past year.
- Nature of Attacks: A substantial 69% report that cyberattacks are growing increasingly targeted.
The most prevalent types of cyberattacks on small businesses include:
- Phishing/Social Engineering: Accounting for 57% of incidents.
- Compromised/Stolen Devices: Representing 33% of attacks.
- Credential Theft: Comprising 30% of reported incidents.
As a business leader, understanding the specific targets and consequences of these attacks is paramount. It allows you to minimize potential risks, enhance the value of your cybersecurity efforts, and even proactively prevent future attacks.
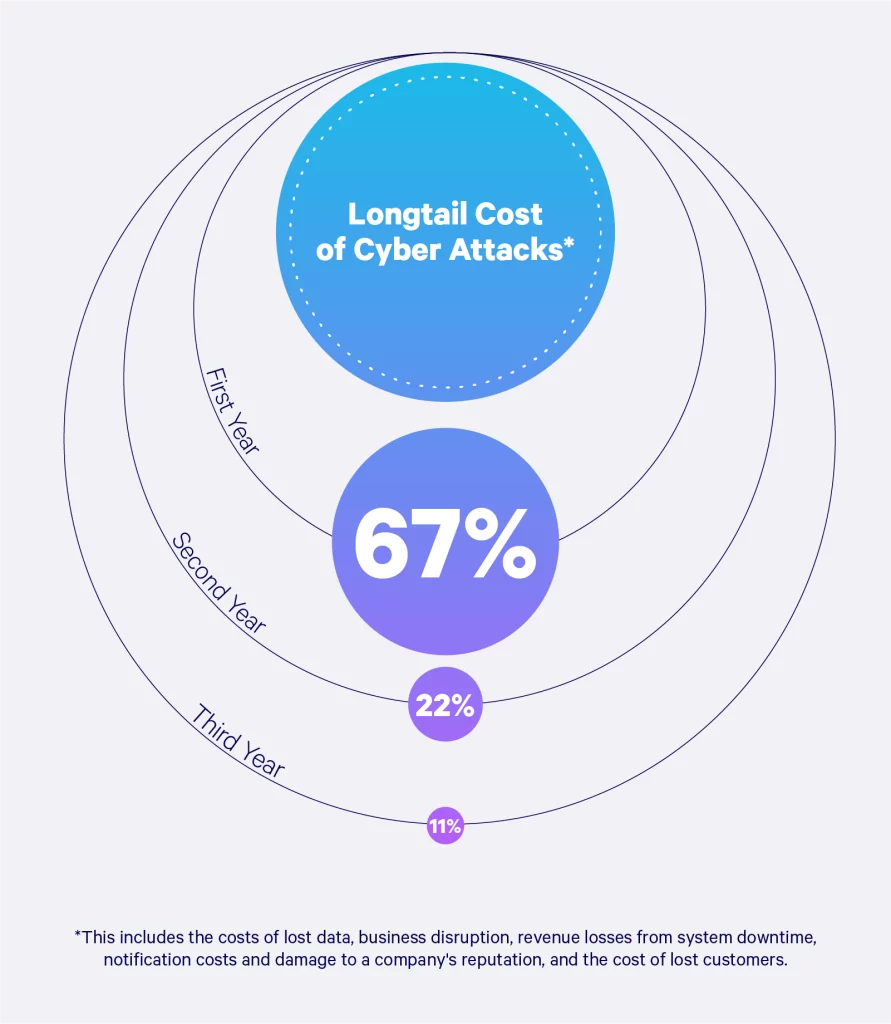
Longtail Cost of Cyber Attacks
The enduring repercussions of a data breach can persist for months to even years, encompassing substantial expenses that often catch companies off guard, as they may not have accounted for them in their initial planning.
These expenses encompass a spectrum of factors, such as data loss, operational disruptions, revenue declines resulting from system downtime, notification expenses, and potential harm to a brand's reputation. In the visual representation below, we delineate the various impacts a business might encounter over a span of three years, starting from the first year post-breach
Impact and Severity of Cyber Attacks
Cyberattacks can have a multifaceted impact on an organization, ranging from minor operational disruptions to significant financial setbacks. Irrespective of the nature of the cyber attack, each consequence carries a cost, whether in terms of money or other resources.
The aftermath of a cybersecurity incident may continue to affect your business for weeks, and in some cases, even months. Below are five critical areas where your organization may encounter adverse effects:
- Financial Losses
- Decreased Productivity
- Reputation Damage
- Legal Liability
- Disruptions to Business Continuity
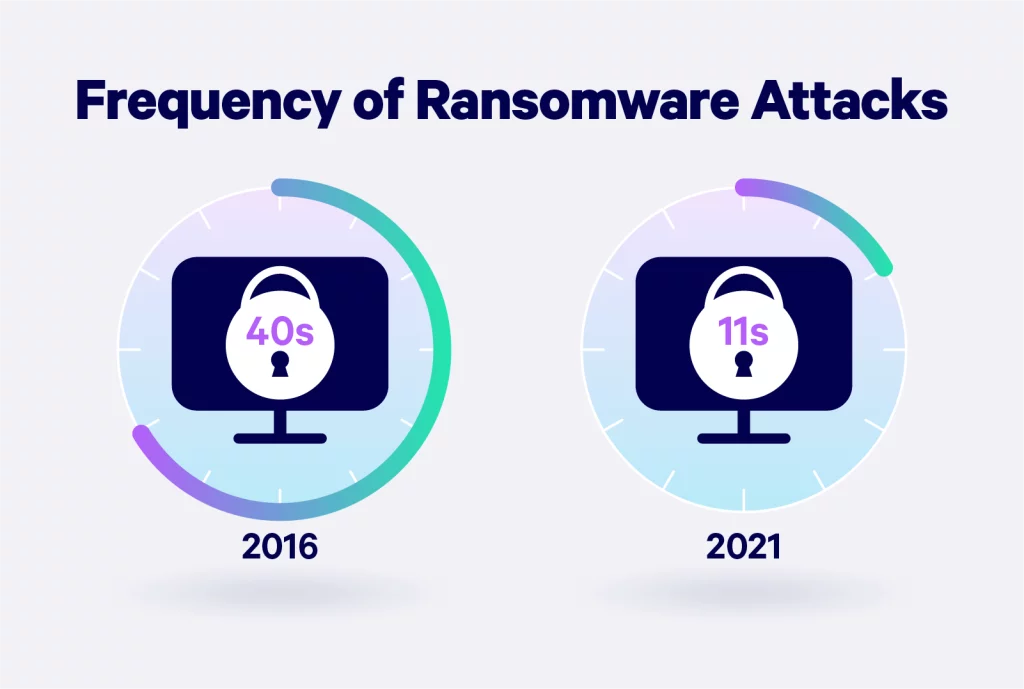
Among the growing concerns in the cybersecurity landscape, ransomware attacks are on the rise. In 2022, a startling 70% of businesses fell victim to ransomware attacks. According to a report by Cybersecurity Ventures, this rate is projected to increase to an attack occurring every 11 seconds by 2023. Ransomware attacks involve the use of malicious software to restrict access to computer systems or data, with the attacker demanding a ransom payment from the victim.
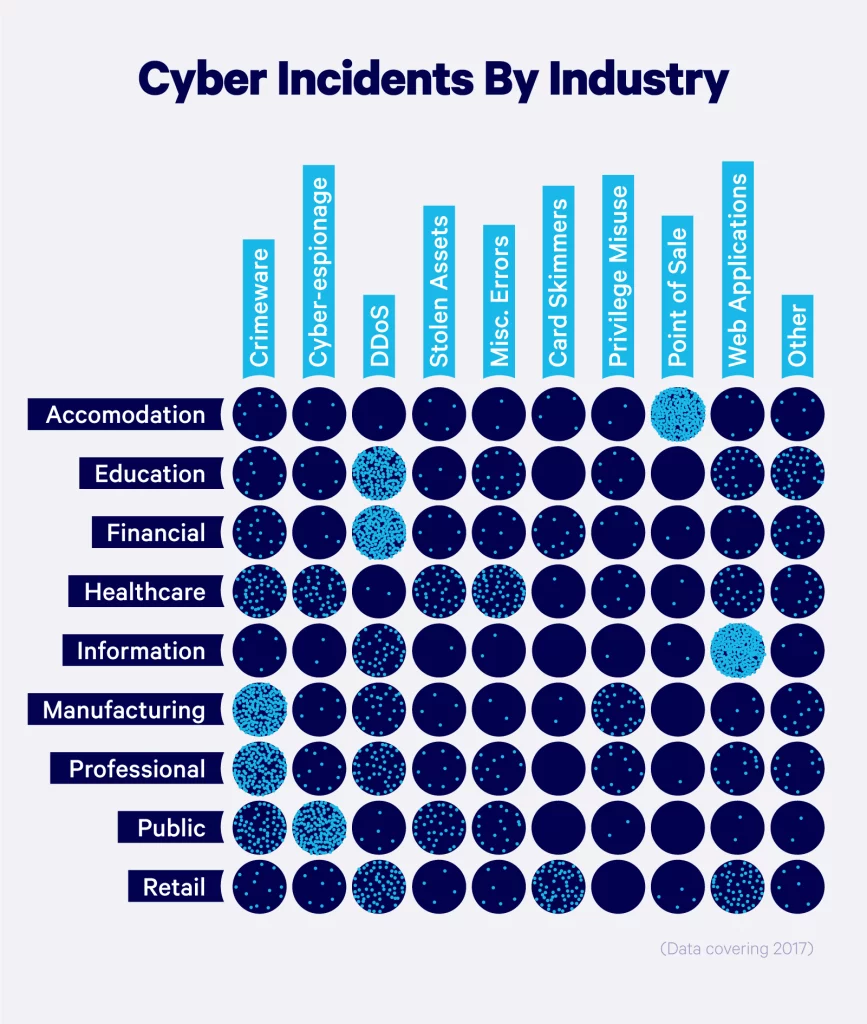
Cyber Attacks by Industry
Certain industries exhibit higher vulnerability to cyberattacks, primarily owing to the nature of their operations. While no sector is entirely immune to data breaches, those most susceptible are businesses deeply intertwined with people's daily lives.
Hackers frequently target companies that store sensitive data or personally identifiable information (PII). Industries particularly vulnerable to cyberattacks include:
- Banks and Financial Institutions: These entities house credit card details, bank account information, and personal customer or client data.
- Healthcare Institutions: Serving as repositories for health records, clinical research data, and patient information, including social security numbers, billing data, and insurance claims.
- Corporations: Corporations hold diverse data ranging from product concepts and intellectual property to marketing strategies, client and employee databases, contract agreements, client presentations, and more.
- Higher Education: These institutions maintain information on enrollment, academic research, financial records, and personally identifiable details like names, addresses, and billing information.
In the visual representation below, we delve into common types of cyber incidents and their varying impacts on various industries.
In the visual below, we break down common types of cyber incidents and the varying impacts on industries.
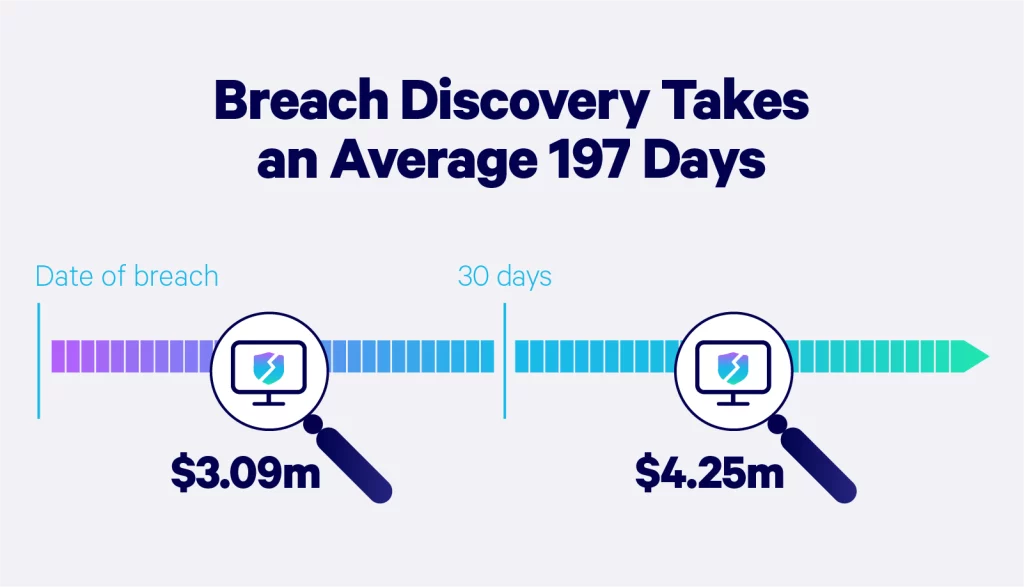
Breach Discovery
Breach discovery is when the company or business becomes aware that the incident occurred. According to IBM, it takes a company 197 days to discover the breach and up to 69 days to contain it.
Companies that contained a breach in less than 30 days saved more than $1 million compared to those that took more than 30 days. A slow response to a data breach can cause even more trouble for your company. It can result in a loss of customer trust, productivity, or major fines.
A data breach response plan is a proactive way to be prepared in the event that a breach does occur. Having a risk management strategy in place to combat incidents such as breaches can minimize the impact on your company and bottom line. An incident response plan, for example, provides guidance for your team during the phases of detection, containment, investigation, remediation, and recovery.
Information Security Spending
Statista Market Report’s revenue in the Cybersecurity market is projected to reach $162 billion in 2023. It is expected to show an annual growth rate from 2023 to 2028 of 9.63%, resulting in a market volume of $256.50 billion by 2028.

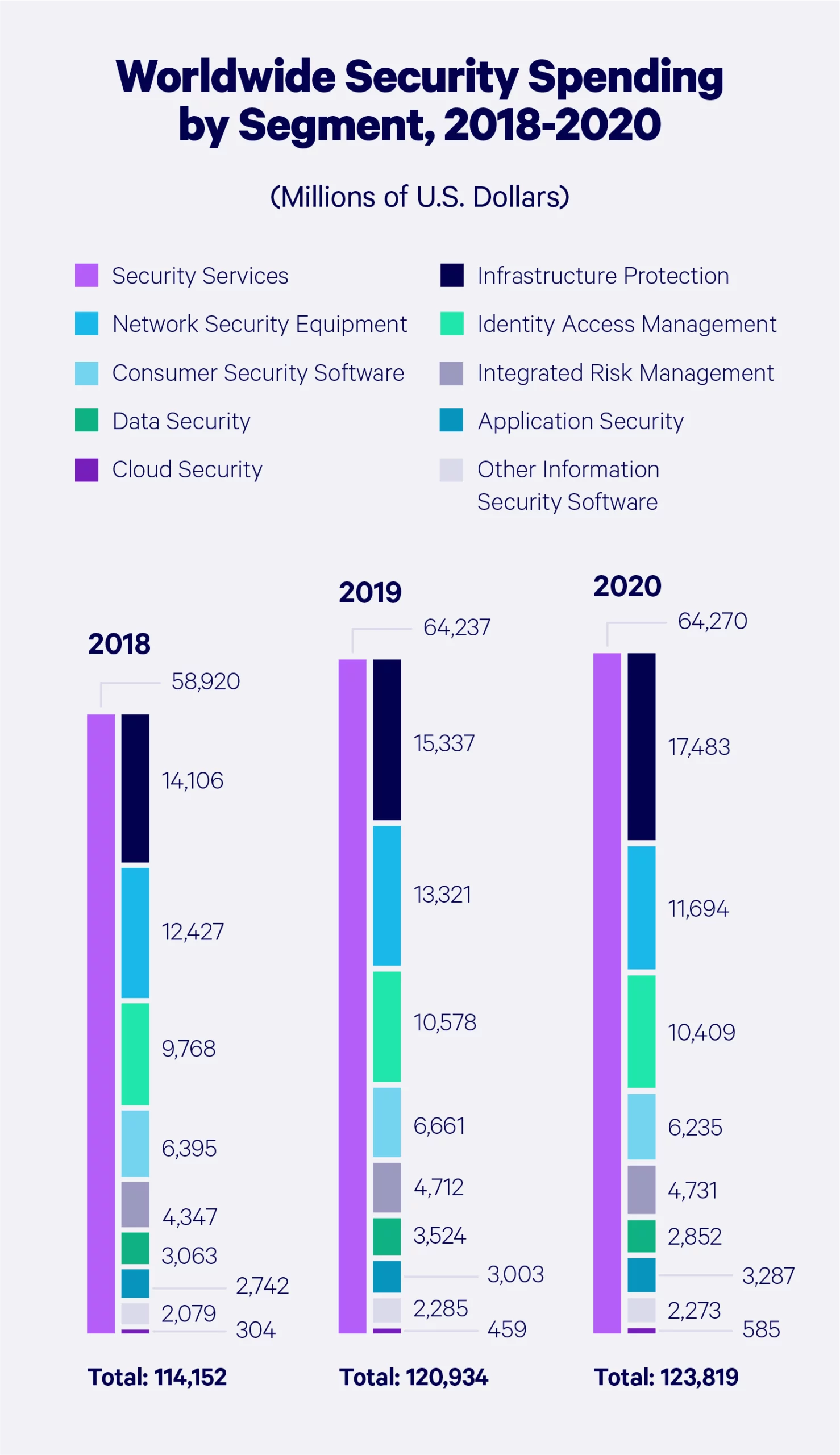
Global Security Spending
Let’s take a look at how cybersecurity spending has grown around the globe — broken down by product or service.
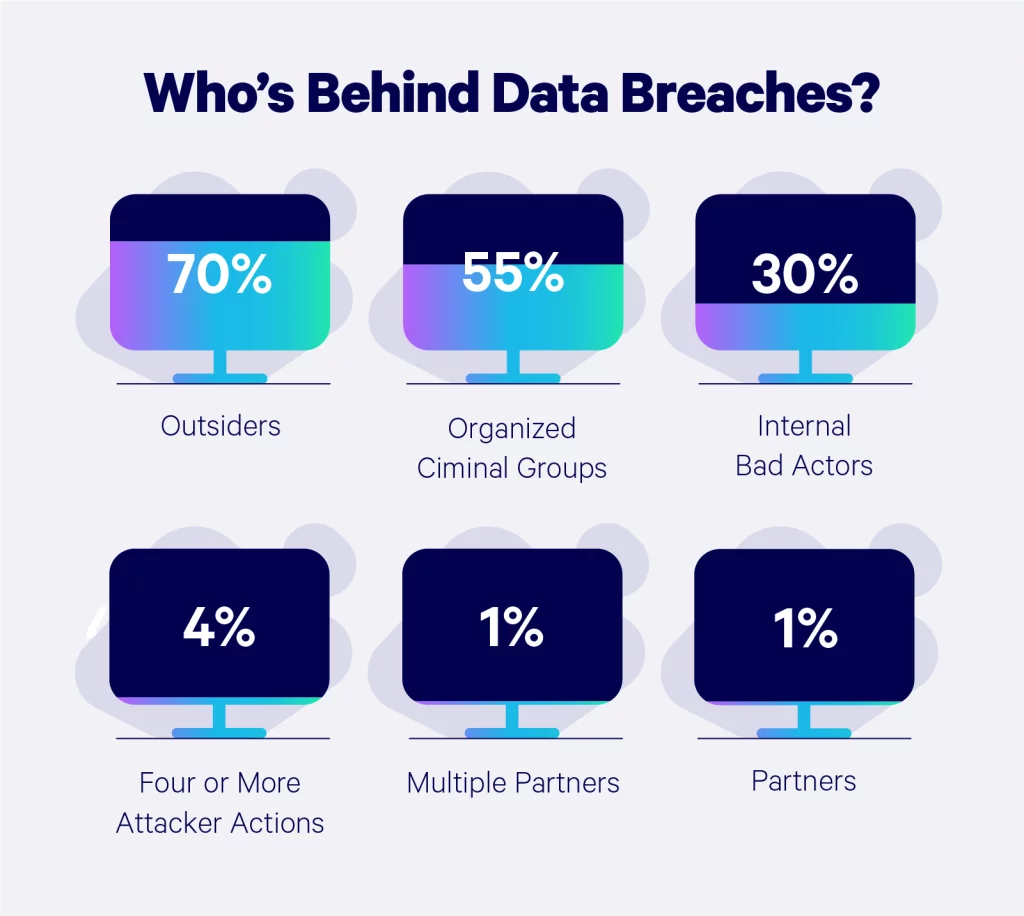
Who’s Behind Data Breaches?
The average person might assume the files on a company database are a bunch of boring documents, but hackers know the hard truth about that hard drive.
According to Verizon’s Data Breach Investigations Report, the majority of cyber attacks are triggered by outsiders, insiders, company partners, organized crime groups, and affiliated groups. We break down the percentages of each:
How to Reduce the Risk of Cyber Attacks
With the increasing threats of hackers mishandling your data, implementing processes to prevent data security breaches is the most responsible course of action after having adequate professional data breach insurance.
Data breach laws vary by state, so depending on where your business is located, there are different factors to take into consideration. Notifications around the breach, what’s covered, and penalties will look different depending on the incidence and state you’re located in.

Sources: Cybersecurity Ventures 1, 2 | IBM | Ponemon | Statista | Verizon | World Economic Forum

